The Common Vulnerabilities and Exposure (CVE) list currently has in excess of 183,000 entries with many thousands more continuously being added, this feels pretty overwhelming for any business to manage.
In better news, the fact is only a small percentage, between 2% – 5% of published vulnerabilities are actually exploited in the wild.
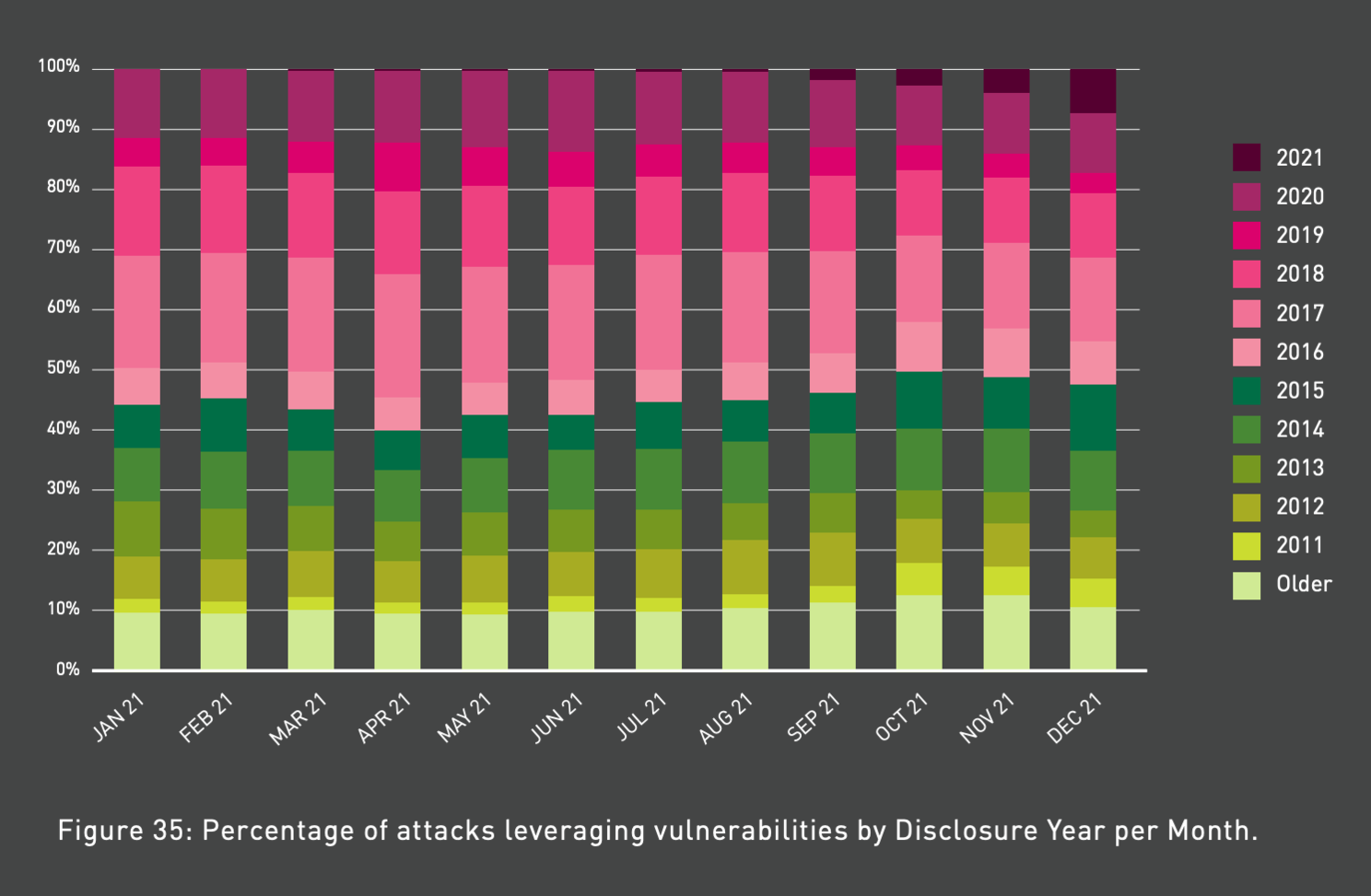
However, the number of attacks leveraging old vulnerabilities is worryingly high. It’s also estimated that half of all internet-facing applications are considered high or critical risk.
The lifecycle of a vulnerability typically starts when flawed code is written and released in a vulnerable state.
Penetration testing is standard practice in most businesses and forms an essential part of a Threat and Vulnerability Management (TVM) program.
However, the use of penetration testing as a sole method for working out whether an environment has been coded securely is still very high. In more mature TVM programs, penetration testing is used as a method that provides assurance an environment is broadly secure, not a method to initially capture vulnerabilities.
Technical and software development teams are on the front line when it comes to protecting your business against cyber security threats.
Ensuring vulnerabilities are not introduced in the first place should be a strong focus for businesses given the considerable risk reduction this provides.
So we know that it’s only a small percentage of known vulnerabilities which either can or are being exploited. We also know that out of the vulnerabilities which are being exploited it’s a very high percentage that have been in the wild for years.
Adopting a multi layered approach inclusive of specialist secure coding training will significantly reduce the introduction of vulnerabilities existing within company environments in the first place.
The exact return on investment (ROI) from providing developer training in secure coding practices is hard to quantify but benefits include:
Staff Retention.
Staff are less likely to leave if training is provided. Recent research from Lorman shows 74% of employees are willing to learn new skills or retrain in order to remain employable, whereas 74% of surveyed employees feel they aren’t reaching full potential at work due to lack of development opportunities. Costs of replacing staff run between 10 & 20% of annual salary. Far more than the costs of training existing staff.
Risk Reduction.
All training participants are able to prevent a number of key issues including SQL injection, the number 1 application security risk and with the average cost of a data breach running at around $9m in the US and £4m in the U.K. a breach caused by these issues can be avoided.
Productivity
The process for deploying applications can be better streamlined, as there are less issues to fix when the code is tested prior to release.
Compliance & Regulatory Obligations
Training helps meet specific requirements within security and compliance standards as well as helping support regulatory obligations.
Responsibility
Training helps support people in their understanding of their specific responsibilities. Many times the industry has seen the blame game after significant breaches where companies start to point fingers at their own people post breach yet in many of those cases the company has failed to provide adequate training that could have prevented the incident from occurring in the first place.
55% of developers revealed that good training has increased their confidence in their coding techniques, while 53% said that good training has allowed them to be more careful when debugging and testing their own code.
Most importantly, 53% believe they have become more mindful of security while writing their code – leading to fewer vulnerabilities, less rework and reduced risk.
Blackfoot is driving its strategy and continued investment of ensuring our consultancy and advisory team are world class experts, highly experienced practitioners who aren’t just highly decorated with certifications and accreditations but have been there and done it for themselves.
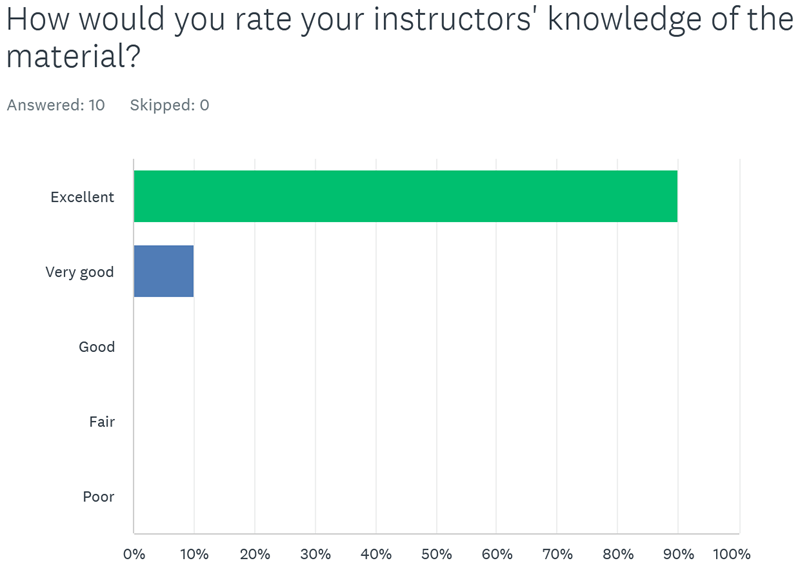
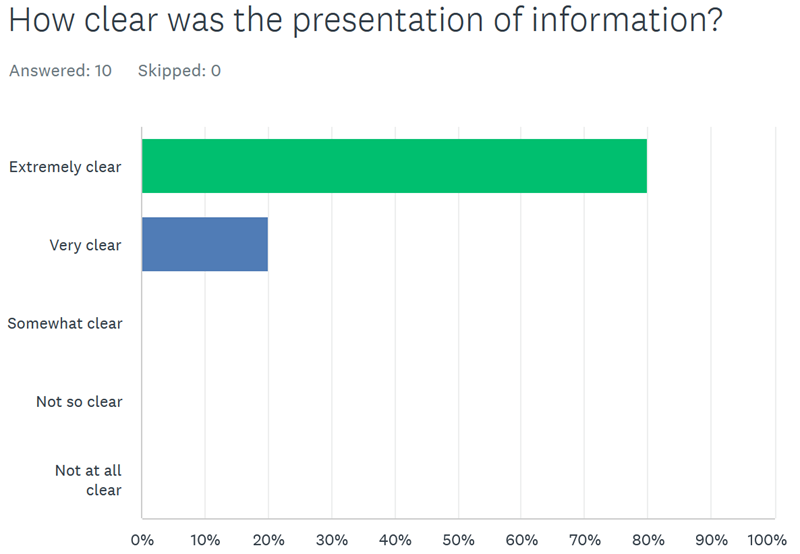
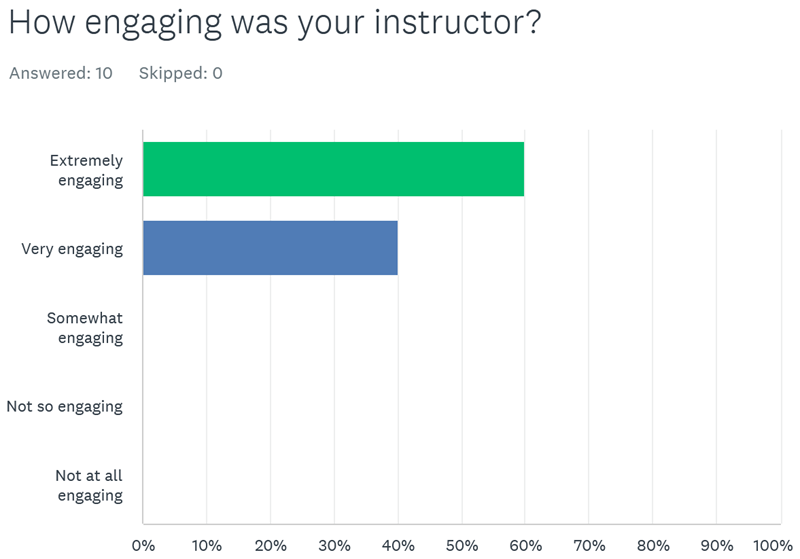
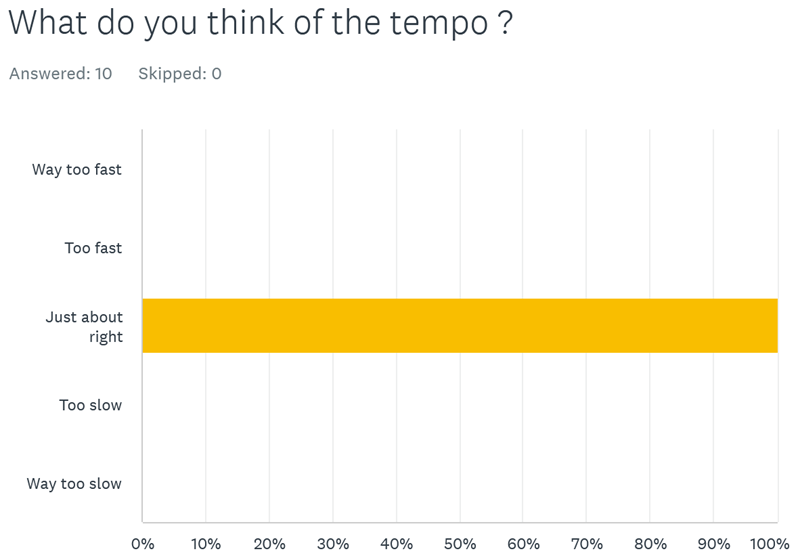
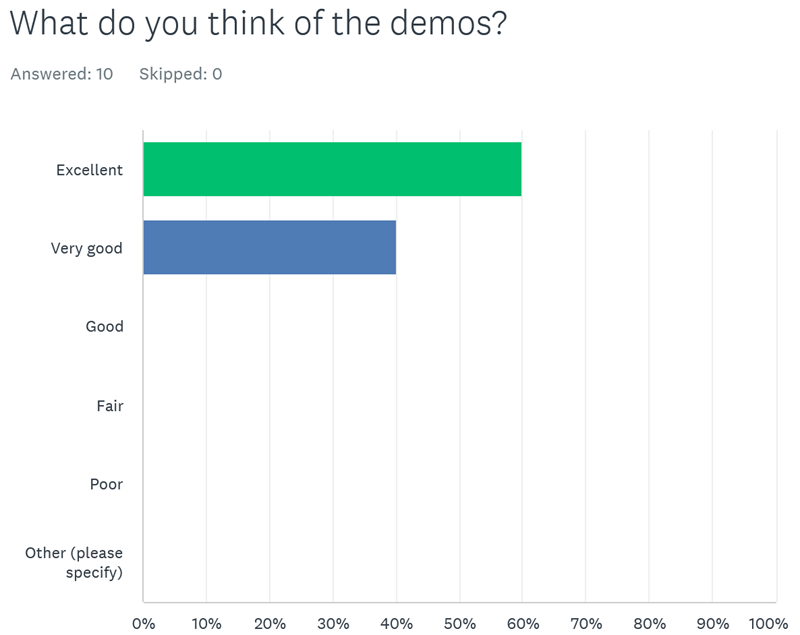
At another successful recent delivery of a series of Blackfoot secure development instructor led training workshops for one of our FTSE250 clients, we asked a number of questions from several attendees across the series of secure development courses, here is how we got on:
Our classroom-based training workshops are designed to provide a solid grounding in the secure software and web development.
The course is intended for software and web developers, especially those developing systems which are internet-facing and/or handle sensitive data such as personal data or cardholder data.
The course raises awareness of many of the most common security vulnerabilities that applications are susceptible to and teaches how to incorporate security throughout the software development lifecycle (SDLC) in order to develop more robust applications
By the end of the course, the trainees had learnt about:
- Basic security concepts
- Designing security into application architectures
- Feature specification and threat modelling
- Types of vulnerabilities to actively prevent
- OWASP Top 10
- Security development and testing tools
- Code reviews and security assurance
Security must be continuous, here are 8 principles of Secure Development & Deployment:
- Secure development is everyone’s concerns
- Keep your security knowledge sharp
- Produce clean and maintainable code
- Secure your development environment
- Protect your code repository
- Secure the build and deployment pipeline
- Continually test your security
- Plan for security flaws



